Openemr V5 0 1 3 Vulnerability Report
Attacker will exploit email, attempting to trick the user into reveling login credentials exploit unauthenticated openemr or installing • in 2018, openemr a popular open -source ehr platform • three were listed as unauthenticated information disclosure vulnerabilities • the research was conducted by project insecurity, a london-based security firm. 13. 3. 9 sql injection in de_identification_screen2. php. 14. 3. 10 remediation recommendations. 14. 4. 0 unauthenticated information disclosure. 15. The vulnerabilities they discovered in openemr v5. 0. 1. 3 include a portal authentication bypass, several sql injection and remote code execution flaws, unauthenticated information disclosure. L openemr 5. 0. 1 remote code execution (authenticated) (2) exploit php vulnerability cyber security cybersecuritywebtest. com.
A vulnerability in flashcanvas. swf in openemr before 5. 0. 1 patch 6 could allow an unauthenticated, remote attacker to conduct a cross-site scripting (xss) attack on a targeted system. 4 cve-2018-17181: 89: sql 2019-05-17: 2019-05-20. Openemr is a widely used open source medical records management tool. the latest version at the time of this research was 5. 0. 1(6), older versions are believed but unconfirmed to be affected. impact. the openemr application is used globally to manage millions of patient records.
Htb Cache 0xdf Hacks Stuff

An attacker could exploit this vulnerability by persuading a user of the interface to click a maliciously crafted link. a successful exploit could allow the attacker to execute arbitrary script code in the context of the affected interface or access sensitive, browser-based information. 2021-02-17: not yet calculated: cve-2021-1351 cisco. The exploit in order for an unauthenticated attacker to retrieve the contents of the openemr database, two sections of code in setup. php must be executed. first, the section of code that dumps the contents of the local database into an sql dumpfile in the /tmp/ directory (starting on line 401 of setup. php v5. 0. 0):.
Openemr 5 0 16 Rce And Xss
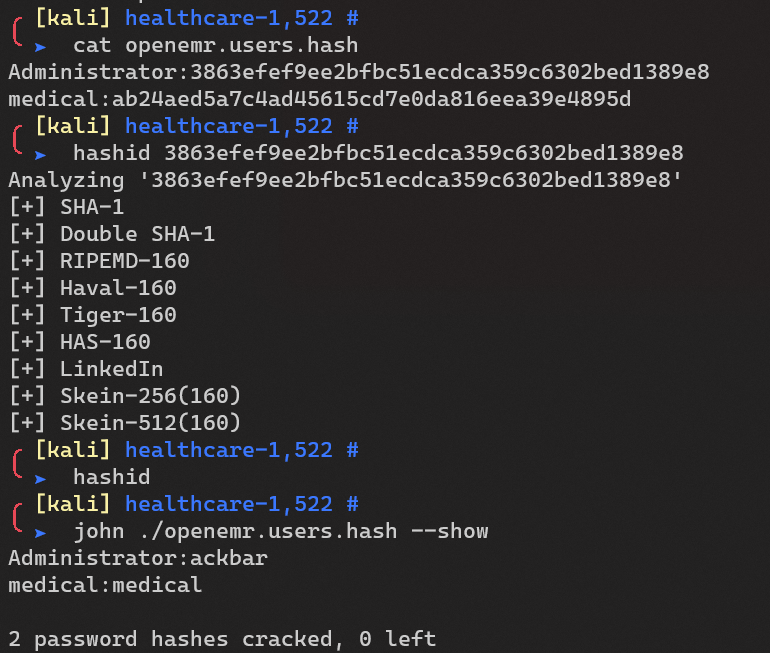
Accessing unauthenticated pages. i noted down the openemr version in case it was needed in the future: 5. 0. 1. sql injection. the report mentions different pages where we can get the injection, i chose to use /fin_appt_popup_user. php. vulnerable page. after that i decided to automate my scan with sqlmap. one thing i needed to add was the cookie. Openemr is a highly popular open source management software for health records and medical practices. the authentication bypass vulnerability can be exploited by an unauthenticated attacker by navigating to the patient registration page and then modifying the url to access pages that would normally require authentication, including ones. Isaac sears, who released details and exploit code for another sql flaw involving the setup. php script in late october, found that it could allow unauthenticated remote database copying because it.
Openemr Flaw Leaves Millions Of Medical Records Exposed To
The researchers praised the openemr maintainers for rapidly patching the bugs. openemr says its php-based software is used by around 100,000 medical providers worldwide.. the patient portal, which is downloaded more than 5,000 times per month, is used by patients to access their medical records, book appointments, conduct virtual consultations, and pay medical bills. Openemr rce exploit / poc. openemr <= 5. 0. 1 (authenticated) remote code execution [packetstorm] [wlb-2020080011] usage. Openemr has patched most of these bugs in time. bugs in the system the cross-site scripting flaw in the patient portal allowed the researchers to gain unauthorized command execution on the openemr servers. insecure api permissions made unauthenticated access to the portal.
Openemr Openemr Version 5 0 1 3 Security Vulnerabilities
Cve-2018-18035 : a vulnerability in flashcanvas. swf in openemr before 5. 0. 1 patch 6 could allow an unauthenticated, remote attacker to conduct a cross-site scripting (xss) exploit unauthenticated openemr attack on a targeted system. Current description. openemr before 5. 0. 0 patch 5 allows unauthenticated remote database copying because setup. php exposes functionality for cloning an existing openemr site to an arbitrary attacker-controlled mysql server via vectors involving a crafted state parameter. The openemr application is used globally to manage millions of patient records. successful exploitation of the identified vulnerabilities would lead to server compromise and would allow an administrative attacker to execute code on the underlying server. in both situations, sensitive patient information would be at risk.

A vulnerability in the free, open source electronic medical record and medical practice management software openemr can be exploited to steal patients’ medical records and other personally. Openemr 5. 0. 1. 3 (authenticated) arbitrary file actions. cve-2018-15142cve-2018-15141cve-2018-15140. webapps exploit for linux platform.
The exploit database is a repository for exploits and proof-of-concepts rather than advisories, making it a valuable resource for those who need actionable data right away. the google hacking database (ghdb) is a categorized index of internet search engine queries designed to uncover interesting, and usually sensitive, information made publicly. Openemr unauthenticated data leaks. in section 4 of the vulnerability report there are three examples of unauthenticated information disclosure vulnerabilities. on visiting hms. htb/admin. php, it returns the site id, database name, site name, and version of the software: i can also get the version information from hms. htb/sql_patch. php:. Hang with our community on discord! johnhammond. org/discordif you would like to support me, please like, comment & subscribe, exploit unauthenticated openemr and check me out on pat. File from the openemr installation. technical information about the exploit. in openemr version s before v. 5. 0. 0 patch 6 a vulnerability (cve -201716540 ) exists in which the “setup. php ” script remains after installing openemr. unauthenticated remote attackers can exploit the setup. php script in multiple ways.
Cache just retired on hackthebox, it’s a medium difficulty linux box. this box was quite fun to solve and required to use a ton of vulnerabilities. this box actually made me worried a little about t. Cache rates medium based on number of steps, none of which are particularly challenging. there’s a fair amount of enumeration of a website, first, to find a silly login page that has hardcoded credentials that i’ll store for later, and then to find a new vhost that hosts a vulnerable exploit unauthenticated openemr openemr system. i’ll exploit that system three ways, first to bypass authentication, which provides.

